Scalable Trust of Next Generation Management (STRONGMAN)
Goals | Activities | People | Papers | Links
Goals
Mechanisms such as
IPsec
allow cryptographically secured communication among nodes and network
elements on the IP Internet. Furthermore, the role of firewalls as
access control and policy enforcement points in such an infrastructure
becomes even more profound. Building a secure next generation
information infrastructure demands automated management of keys and
policy, for reasons of both risk management (in the small) and
automatic configuration of boundary controllers (as the information
infrastructure is scaled to an environment with many millions of
nodes).
By automated management, we mean the translation of a high-level
security policy into actions which support that policy at every
relevant level of the information infrastructure. Thus, security
policy must be reflected in decisions about trust of sources of
information, for example in the acceptance of a remote invocation. Our
belief is that the investigation of scalable automated trust
management will lead to a huge leap forward in the ability of an
organization to deploy an auditable error-free realization of network
infrastructure meeting security policy goals.
The basis of our approach is the
KeyNote
trust management system
being investigated at the
University of Pennsylvania
and
AT&T Labs -- Research.
KeyNote is a compact simplified representation of trust relationships
based on the ideas of the AT&T PolicyMaker system; trust relationships
are specified in terms of a symbolic language which when executed
results in exchanges of cryptographic credentials which map the trust
relationships into allowed and disallowed actions. In the proposed
effort, KeyNote will be integrated with IPsec and a firewall package
to allow automatic configuration of groups of IP routers under control
of a specified security policy. The novelty of this approach is that a
high-level security policy can be expressed in a ``meta-KeyNote''
which generates KeyNote expressions (perhaps millions on a large
information infrastructure) which are in turn mapped to specific
secure exchanges to control actions at, among other locations,
boundary controllers.
Activities
- Developed FileTeller, a system for buying and selling storage
on the network utilizing a micropayment scheme.
- Added KeyNote support in isakmpd, a free implementation of
the IPsec IKE
key management protocol. This is being distributed as part of the
OpenBSD system since 1999. See the
isakmpd.policy
man page for more details.
- Added KeyNote support in the Apache
web server's mod_ssl module (an implementation of the
SSL/TLS
protocol using the
OpenSSL library. We intend to
release this software in the summer of 2001.
- Added KeyNote support in the OpenSSH
implementation of the
Secure Shell
protocol. This is still work in progress (as of summer 2001).
- Developed the distributed firewall concept (in
collaboration with Steve Bellovin, AT&T Labs -- Research) and built a
prototype system, based on IPsec and KeyNote policies, for scalable,
fine-grained network access control. See the Papers section below.
- Developed a transparent firewall that can enforce
network-layer security policies in conjunction with IPsec. We are
working on integrating this with the distributed firewall concept. See
the Papers section below.
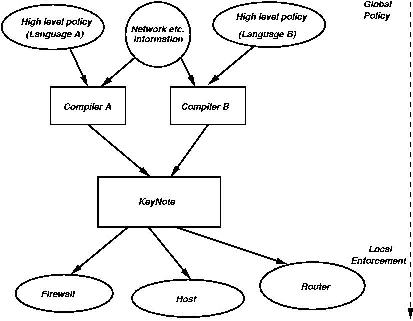
- We have developed a decentralized architecture for managing the
security policy of a large network. Our approach allows multiple
high-level policy languages to be used simultaneously in expressing
the security policy requirements for any number of applications,
networks, nodes, and users. The high-level expressions are compiled to
KeyNote credentials, that are then distributed to end-users. Policy
Enforcement Points find out the policies that affect them on an
as-needed basis, greatly reducing the amount of resources needed to
store and process policies.
People
Papers
- "TAPI: Transactions for
Accessing Public Infrastructure"
- Matt Blaze, John
Ioannidis, Sotiris Ioannidis, Angelos D. Keromytis, Pekka Nikander,
and Vassilis Prevelakis. To appear in the Proceedings of the 8th
IFIP Personal Wireless Communications (PWC) Conference. September
2003, Venice, Italy.
- "Design and Implementation of
Virtual Private Services"
- Sotiris Ioannidis, Steven
M. Bellovin, John Ioannidis, Angelos D. Keromytis, and Jonathan
M. Smith. In Proceedings of the IEEE International Workshops on
Enabling Technologies: Infrastructure for Collaborative Enterprises
(WETICE), Workshop on Enterprise Security, Special Session on Trust
Management in Collaborative Global Computing. June 2003, Linz,
Austria.
- "WebDAVA: An Administrator-Free Approach To
Web File-Sharing"
- Alexander Levine, Vassilis Prevelakis, John
Ioannidis, Sotiris Ioannidis, and Angelos D. Keromytis. In
the Proceedings of the IEEE International Workshops on Enabling
Technologies: Infrastructure for Collaborative Enterprises (WETICE), Workshop
on Distributed and Mobile Collaboration. June 2003, Linz,
Austria.
- "Secure and Flexible Global File Sharing"
- Stefan Miltchev, Vassilis Prevelakis, Sotiris Ioannidis, John
Ioannidis, Angelos D. Keromytis, and Jonathan M. Smith.
In Proceedings of USENIX 2003 Annual Technical Conference, Freenix
Track, pp. 165
- 178. June 2003, San Antonio, TX.
-
``The STRONGMAN Architecture'',
- Angelos D. Keromytis, Sotiris Ioannidis, Michael B. Greenwald, and Jonathan
M. Smith. In the Third DARPA Information Survivability Conference and Exposition (DISCEX III), Washington, D.C.
April 22-24, 2003
- "S
ub-Operating Systems: A New Approach to Application Security"
- Sotiris Ioannidis, Steven M. Bellovin, and Jonathan M. Smith. In
Proceedings
of the ACM
SIGOPS European Workshop. September 2002, France.
- A Study of the Relative Costs of Network Security Protocols
-
Stefan Miltchev, Sotiris Ioannidis, and Angelos Keromytis. In Proceedings of USENIX 2002 Annual Technical Conference, Freenix Track. June 2002, Monterey.
- Fileteller: Paying and Getting Paid for File Storage
- John Ioannidis, Sotiris Ioannidis, Angelos D. Keromytis, and Vassilis Prevelakis. In Proceedings of Financial Cryptography (FC) 2002. March 2002, Bermuda.
- Building a Secure Web Browser
- Sotiris Ioannidis and Steve. M. Bellovin. In Proceedings of USENIX 2001 Annual Technical Conference, Freenix Track. June 2001, Boston.
- "Trust Management for
IPsec"
- Matt Blaze, John Ioannidis, and Angelos
D. Keromytis. In Proceedings of the Internet Society
Symposium on Network and Distributed Systems Security (SNDSS)
2001, pp. 139 - 151. February 2001, San Diego, CA.
- "Implementing a Distributed
Firewall"
- Sotiris Ioannidis, Angelos D. Keromytis,
Steve Bellovin, and Jonathan M. Smith. In Proceedings of the ACM
Computer and Communications Security (CCS) 2000, pp. 190 - 199.
November 2000, Athens, Greece.
- "Implementing Internet
Key Exchange (IKE)"
- Niklas Hallqvist and Angelos D.
Keromytis. In Proceedings of the USENIX 2000 Annual Technical
Conference, Freenix Track, pp. 201 - 214. June 2000, San Diego,
CA.
- "Transparent Network
Security Policy Enforcement"
- Angelos D. Keromytis and
Jason Wright. In Proceedings of the USENIX 2000 Annual Technical
Conference, Freenix Track, pp. 215 - 226. June 2000, San Diego,
CA.
- "Trust Management and
Network Layer Security Protocols"
- Matt Blaze, John
Ioannidis, and Angelos D. Keromytis. In Proceedings of the 1999
Security Protocols International Workshop, April 1999, Cambridge,
England.
- "DSA and RSA Key and
Signature Encoding for the KeyNote Trust Management
System"
- Matt Blaze, John Ioannidis, and Angelos
D. Keromytis. Request For Comments (RFC) 2792, March
2000.
- "The KeyNote
Trust-Management System, Version 2"
- Matt Blaze, Joan
Feigenbaum, John Ioannidis, and Angelos D. Keromytis. Request For
Comments (RFC) 2704, September 1999.
Useful Links

